The awareness campaign was a phenomenal success: it raised 115 million dollars in six weeks and it brought much needed awareness for the little-known disease Amyotrophic Lateral Sclerosis (ALS).
ALS breaks down nerve cells, weakens muscles and impairs basic functions. Campaigning has been essential in order to raise funds, enabling researchers and scientists to work on a cure. Participants stated that, for a short moment when the ice cold water hits the body, the functions shut down and it feels as if you can’t breathe. A split second of nervous system paralysis.
In the autumn of 2016, millions of internet users were affected by the Mirai Botnet incident, where attackers used an IoT botnet composed of more than half a million compromised standard routers and other IoT devices to take down high profile websites like Twitter, Netflix, and Airbnb. A few hours of Internet paralysis.
In order to help explain the risks behind the current IoT trend, this article draws a comparison between the human body and an IoT system. An IoT system is a hugely complex organism. Like the human body, it needs to work in harmony with all interfaces aligned. Within an IoT system, the cloud acts as the brain and the power supply like the heart.
Thousands of sensors within IoT devices act as eyes (cameras), sensitive skin (temperature and pressure sensors), and ears (microphones). The nervous system within this organism is a network made up of routers and switches. So far, the nervous system of the IoT has received very little attention. Its integrity, however, is essential for any IoT system to function.
Just like the human body, an IoT organism needs to be protected from within – by design – from outside threats. It is not enough to protect the brain and leave the nervous system exposed to threats. Unlike the patching approach of many software solutions, which are applied after attacks have been detected, Infineon’s security hardware aims to strengthen an IoT system from within and to fortify the organism’s immune system, making it harder to attack in the first place.
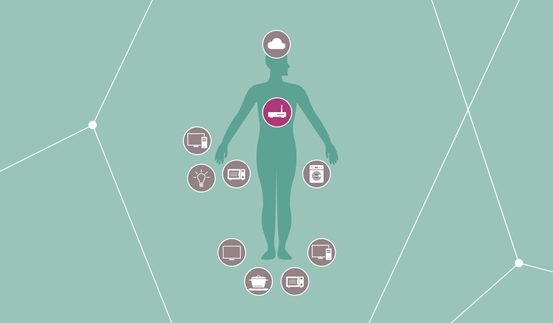
Figure 1: Network equipment: the nervous system of the connected world
Cyber attacks are a massive threat to ICT growth
“Where there is most light, the shades are deepest,” wrote J W Goethe. Nearly 250 years later, this statement is more valid than ever when looking at the opportunities and risks in the IoT market: by 2020, IDC predicts, the IoT will grow to represent 50 trillion GBs of data, running through 25 billion embedded and intelligent systems and connecting 4 billion people.
With an estimated revenue potential of $4tn, the IoT is one of the most exciting developments of the 21st century. For the industry, this translates into very real profit; with analysts predicting that vendor revenues tied to IoT will grow at three times the rest of traditional ICT spending.
Compromised networks and the risk associated with the growing number of cyber attacks and data breaches can slow down the spectacular rise of IoT and have a huge impact on the ICT sector. In fact, weak security can bring an IoT-based network to a grinding halt. Less than a year ago, the Mirai Botnet incident really awakened the public to the possibility of IoT attacks.
On October 21st 2016, attackers used an IoT botnet composed of more than half a million compromised routers and other IoT devices to take down high profile websites like Twitter, Netflix, and Airbnb. This was a real life scenario that took place just 12 months after the security experts Charlie Miller and Chris Valasek hijacked their car remotely and drove it off the road.
Two different applications with the same upsetting result: once attackers gained access through the network and the cloud, they had an unsettling amount of control over the entire system. An unprotected nervous system was manipulated and used as back door to access and control the IoT system’s brain.
 Figure 2: Mirai attack flow description
Figure 2: Mirai attack flow description
Protecting the IoT’s nervous system
Security threats are a reality and a lot of emphasis has been placed on the vulnerabilities when it comes to the ‘things’ in Internet of Things. It’s easy to see why the focus is on the many new applications that are flooding the market. Keeping an inventory and managing all connected devices linked to your private or corporate network is critical and many security companies offer solutions to keep on top of this.
For Infineon, it is essential to look at the whole IoT organism and to provide security by design. Hardware based security, which is part of the overall system architecture and includes routers, switches as well as the cloud and the connected devices, is the best way to provide sustainable protection against outside attacks. By not paying attention to designing networks with built-in, hardware-based security capabilities, businesses are placed at risk.
Unfortunately, these problems are likely to grow in an increasingly connected world: attackers exploiting vulnerabilities to gain access and control over devices and then move laterally to gain access to valuable data and systems. If attackers can gain access to the cloud, they effectively access the brain of IoT.
The operators and stakeholders of the network and the cloud are often different but they all have a mandate to provide a secure infrastructure to counteract an IoT network getting attacked and successfully compromised. If the cloud is attacked, the system’s brain may die and the connected things are rendered useless. Infineon can help network equipment manufacturers and cloud providers to secure today’s connected applications.
Why software protection just isn’t enough
The motivation behind most cyber attacks is to take control – Control of hardware, software and of data. Any organisation, whatever its size or line of business, can be targeted. In the case of ransomware, after a successful breach and access to the systems, the data is held hostage through encryption and released only upon payment.
Attackers will find a vulnerability in the software or an endpoint that they can exploit to access the IoT system. Software patches and over-the-air anti-virus updates are generally used to counter these old-fashioned attacks.
Today’s threat reality already looks different. What is more damaging than accessing a system and controlling the data that runs through it? Doing it permanently and remaining undetected while doing so. The nature of attacks on IoT systems is changing – attacks now go deeper than the operating system layer, into the actual firmware of the devices, which makes the attack unpatchable with software.
Once an attacker has compromised the firmware, they can establish permanent control and make their attack nearly impossible to remove remotely. By now, comparable toolkits are available to the public community on the market. Cyber attacks have developed into highly profitable, criminal businesses, where the latest, often state-developed spying toolkits are cloned and offered for sale.
Using these sophisticated tools, cyber terrorists can access public and private sector network routers to get administrative access to sensitive data. For network equipment manufacturers and IoT system operators, this creates a new set of challenges as they find themselves exposed to vulnerabilities that impact revenue generation, harm reputation and threaten business cases.
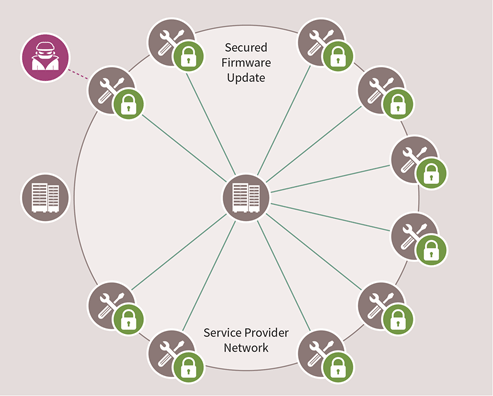
Figure 3: Blocking the Mirai attack
How to implement a hardware-based solution
The good news is that firmware attacks can ben prevented by using hardware-based security solutions, such as the Trusted Platform Module (TPM). Hardware is the strongest protection a network can have, as secure semiconductor technology is, by design, tested under security parameters, constantly exposed and challenged by the latest level of attacks on the market.
Infineon, together with a large network of specialised partners, can support equipment manufacturers and network operators in protecting their own and their customers asset from cyber attacks.
Using hardware security minimises vulnerabilities and maximises sustainability. Returning to the image of an IoT system being like the human body, chip-based security solutions strengthen the system’s immune system, rather than sticking on a bandage.















