To counter the threat of a device and its precious data becoming hacked, several popular asymmetric and symmetric encryption protocols are now routinely used to protect data. However, in addition to protecting data, the device must be protected against hardware-oriented attacks.
This article by Mark Patrick, Mouser Electronics, introduces embedded security techniques and discusses the imminent threat from post-quantum cryptography, particularly for Internet of Things (IoT) and Industrial Internet of Things (IIoT) devices deployed today.
Our connected world
The use of embedded systems in a wide range of industrial equipment and consumer appliances is a phenomenon that has been around for a while. The advent of the microcontroller heralded the start of the embedded era, with everything from central heating thermostats and dishwashers to automobiles and spacecraft making full use of their flexible and low-cost features. However, securing microcontrollers from a digital perspective has been featured in engineering specifications only recently. As isolated islands of compute and control, embedded systems were self-contained and relatively safe from external adversaries. However, the concept of connecting devices and systems, particularly with the fast trend toward IoT, opened these embedded systems to the global internet. For a new breed of hackers and adversaries, the growing numbers of connected devices presented an opportunity to learn new tricks and hone their skills. However, it wasn’t just about attempting to access such connected systems; it also reawakened interest in compromising systems using a variety of physical and electrical intrusion attacks.
Embedded security basics
Figure 1 highlights the primary methods adversaries use to infiltrate and take control of an embedded system. As illustrated, the range of “attack surfaces” and “attack vectors” encompasses both hardware and software from local and remote actors.
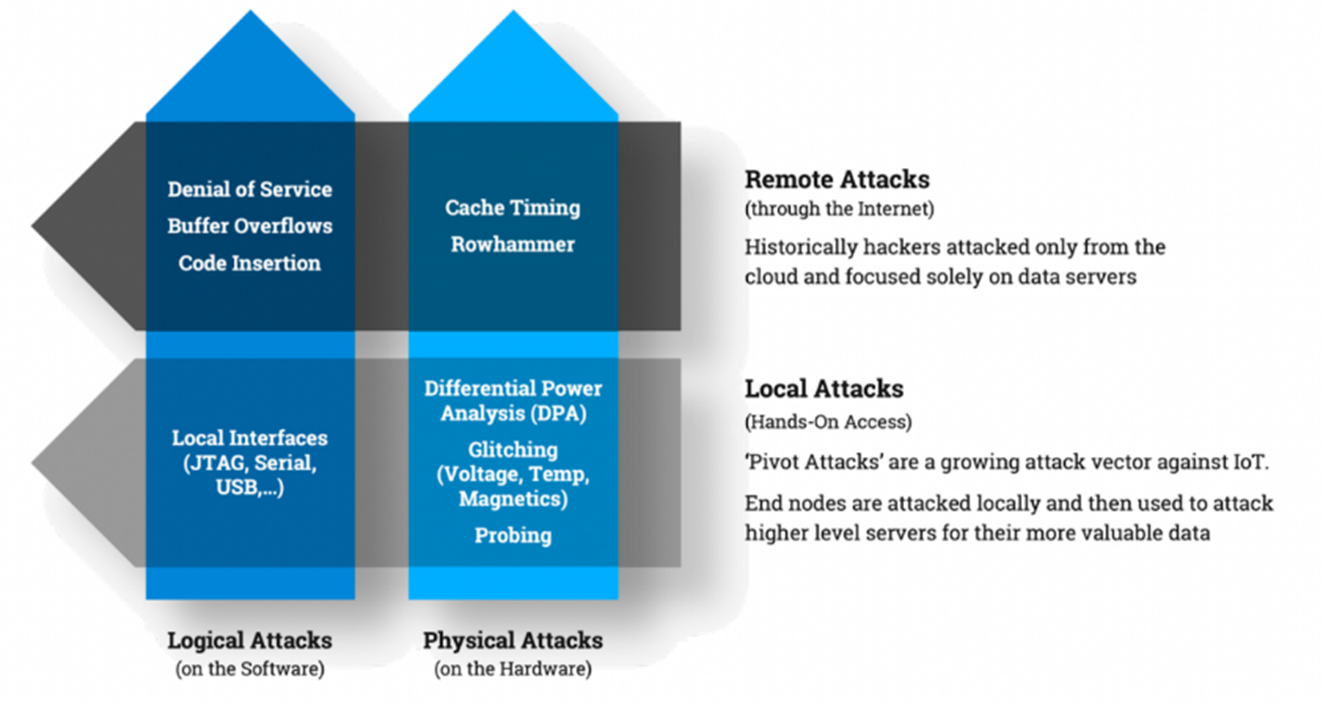
Figure 1: Attacks on an embedded system can come from multiple sources. (Source: Silicon Labs)
When considering attack surfaces, it is important to note that an adversary might not wish to compromise solely the device under attack, instead using it to gain access to the device’s broader network. In that way, an attack will potentially have more profound and wider consequences than simply compromising a single device.
Before we delve into the technical concepts behind embedded security, let’s consider the landscape and reasons for security. Security is an overused word, so what exactly do we mean when referring to the security of an embedded system such as an IoT device? Essentially, there are two goals: Protect the device from being attacked or being used to stage an attack and protect the device’s information. Also, an attack might not necessarily be targeted to compromise or disrupt the device’s operation but to eavesdrop on communications, gain access to commercially sensitive information and passwords, or learn how the system functions.
Maintaining information and data security has many factors, from the privacy of user details and geolocation data to the device manufacturer’s intellectual property and protecting their brand value. In recent years, there have been notable security hacks involving equipment from globally recognised brands that resulted in significant financial consequences.
With the rapid adoption of the IoT/IIoT, governmental and industrial bodies have quickly recognized the threat to embedded devices and provided embedded developers a range of guidelines, such as the EU’s Cybersecurity Strategy for the Digital Decade, the UK’s Product Security and Telecommunications Infrastructure Act, and the ioXt Alliance.
In the following sections, we’ll investigate some of the methods adversaries use to compromise embedded devices and how organizations and engineers can reduce the attack surfaces. We’ll also explore the cryptographic techniques of encryption and authentication and how they underpin the security of an embedded device.
Understanding the attack surface and exploit methods
To help guide developers, the ioXt Alliance has published a Security Pledge (Figure 2), highlighting eight principles, of which secure interfaces is just one consideration.
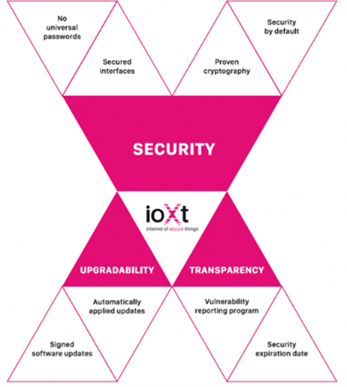
Figure 2: The ioXt Security Pledge highlights eight key priorities for IoT product security, upgradability, and transparency. (Source: ioXt)
Logical attacks through interfaces: During development, the engineering team may routinely use several hardware interfaces and serial ports (e.g., JTAG, UART, I²C, USB) for programming and debugging. However, leaving these interfaces and ports open as the device goes into production represents a potential attack vector to an adversary with physical (invasive) access to the device. Accessing these ports enables access to the software operation and allows the replacement of the device’s firmware.
Probing: This method seeks an attack surface on the hardware at a PCB level. Probing involves examining the hardware behaviour of the device to capture voltage levels, analogue and digital signals, and activity on serial buses and GPIO ports.
Tamper protection: Tamper-protection features are increasingly incorporated into security hardware and software to identify that a hacker is repeatedly attempting to discover a way to force the firmware to behave unexpectedly and become vulnerable to attack.
Glitching: In this method, adversaries purposefully glitch the power rails, forcing the microcontroller into an unexpected and vulnerable state. This approach requires physical access to the device’s PCB. The aim is to put the microcontroller into a condition that opens previously protected ports or bypasses established security protocols and methods.
Differential power analysis: Differential power analysis (DPA) is one of several “side-channel” attack methods (Figure 3). Although some DPA attacks do not require access to the device’s PCB, they do require the device to be close or to have access to the power supply. A side-channel attack aims to bypass any of the device’s encryption or authentication methods by observing some of the device’s operation, such as the power supply or electromagnetic interference (EMI).
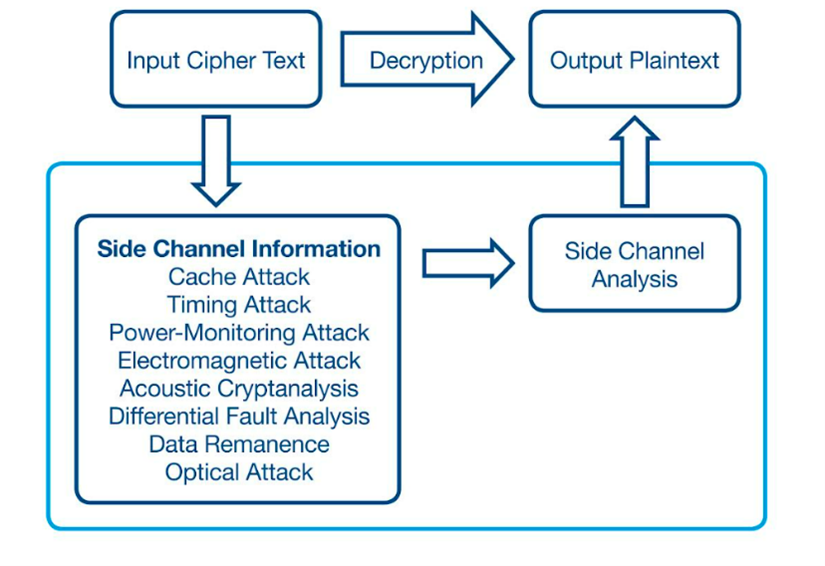
Figure 3: A high-level overview of side-channel attack vectors. (Source: Mouser Electronics, adapted from R. Vanathi and SP. Chokkalingam. “Side Channel Attacks in IaaS and Its Defense Mechanisms.” International Journal of Engineering and Advanced Technology 8, No. 3S (February 2019): 559.)
By monitoring the electromagnetic signals and voltage rails of a microcontroller while performing cryptographic functions, it may be possible to determine the cryptographic keys used. Although initially, this approach required expensive test equipment, the range of low-cost specialist tools available to the adversary community has increased considerably.
Figure 4 illustrates a simple power analysis attack on an embedded device performing a cryptographic function. By monitoring the voltage fluctuations of the microcontroller’s supply, it is possible to determine the calculations it is performing.
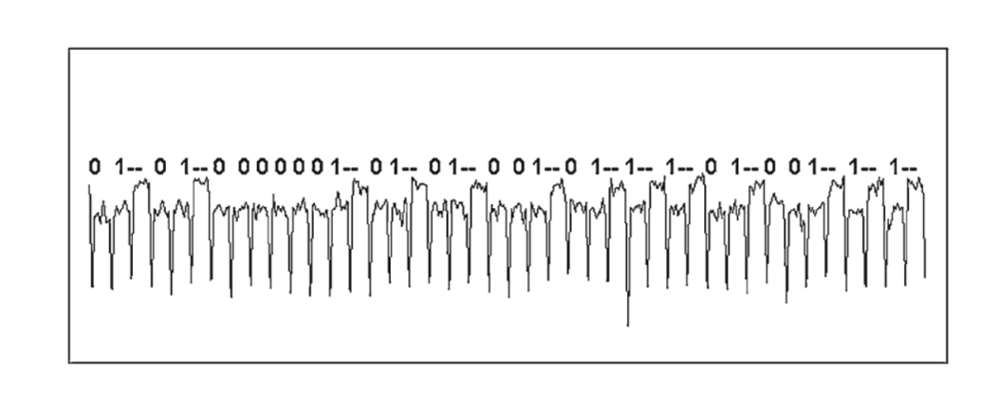
Figure 4: The voltage trace of a microcontroller performing a cryptographic function. (Source: Paul Kocher, Joshua Jaffe, Benjamin Jun, and Pankaj Rohatgi. “Introduction to differential power analysis.” Journal of Cryptographic Engineering 1 (2011): 12. https://www.doi.org/10.1007/s13389-011-0006-y.)
Encryption and Public Key Infrastructure
Encryption and decryption are fundamental techniques for provisioning security routines for embedded systems. Part of these techniques involves using a cipher, an algorithm to convert information into encrypted cipher text. The information could be virtually any plain text, from a password to sensor data. An encryption algorithm requires a key, and for symmetrical algorithms, such as the popular Advanced Encryption Standard (AES), the key used to encrypt the information is also required to decrypt it back into its plain text. AES has been around for over two decades and is in widespread use. AES started with a 128-bit key length but has evolved into a 256-bit key length (AES-256). Theoretically, adversaries with enough computational power could crack any information encrypted with AES-256. However, some estimate that such a “brute force” attack requiring each of the possible 2 trillion key values would take 2 × 1061 years!
Although AES is extremely popular, the one challenge associated with a symmetrical algorithm is that the key must be shared among all related devices. To counter that issue, the RSA algorithm—named after its founders Rivest, Shamir, and Adleman—uses a pair of keys, public and private. RSA established the concept of a public key infrastructure (PKI), where public keys can be widely distributed (Figure 5).
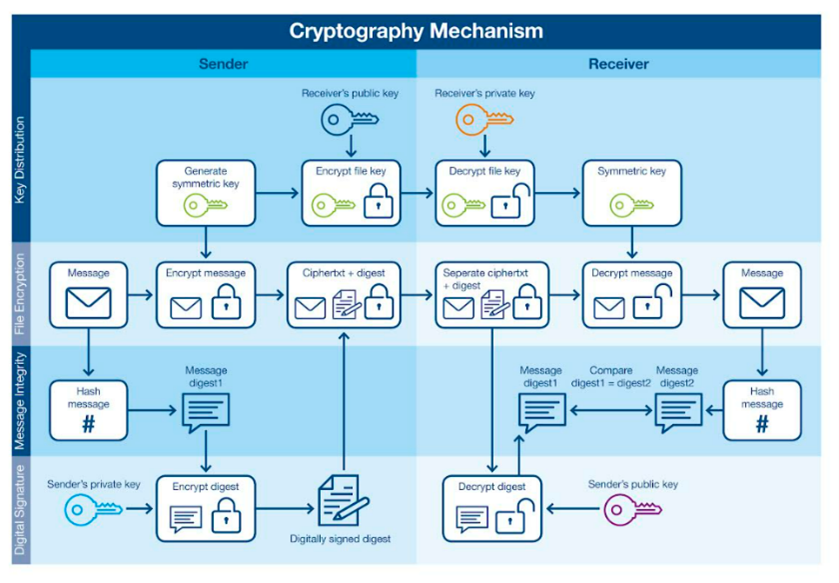
Figure 5: The cryptographic process of a PKI using RSA.
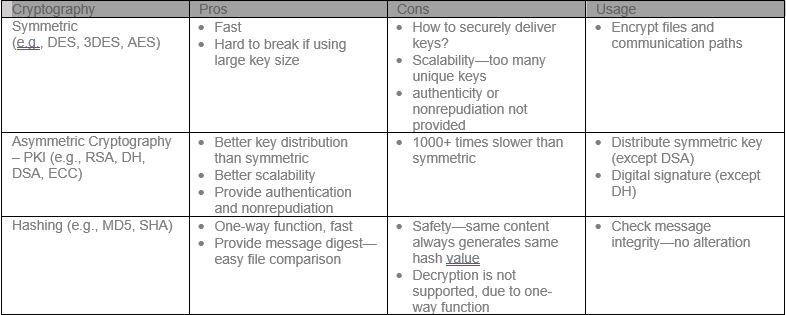
Another cryptographic algorithm is the secure hashing algorithm (SHA), which creates a unique short-form identification, termed a hash digest, of a file. Any changes to the file, even a single character, would result in a different hash digest. SHA algorithms are used for various applications, from validating a software update file or digital signatures. Table 1 highlights the differences between the different cryptographic techniques.
Table 1: A summary of the differences and usage of AES, RSA and SHA.
Embedded Security Functionality Showcase
Many microcontrollers now come equipped with a comprehensive set of security functions. Examples include the Silicon Labs EFR32BG24family of Bluetooth-enabled wireless system-on-chips and the LS00 and LS60 families of Microchip Technology PIC32CMseries microcontrollers.
The EFR32BG24 features many of Silicon Labs’ Secure Vault security functions, including cryptographic accelerators, a true random number generator (TRNG), secure boot with root of trust, anti-tamper, and DPA countermeasures. The hardware cryptographic accelerator complements the device’s high-performance, 32-bit Arm Cortex-M33 core and supports AES-128, AES-192, and AES-256 symmetric key algorithms. It also supports the range of SHA hashing algorithms used for digital signatures. The EFR32BG24’s security capabilities incorporate Arm TrustZone technology, an industry-respected foundational approach to reducing the potential for attack by isolating the critical security firmware, assets and private information from the rest of the application.
Microchip PIC32M LS00 and LS60 ultra-low-power microcontrollers also incorporate Arm TrustZone technology and offer security functions like symmetrical and asymmetrical accelerators, secure boot, and secure key storage elements.
Post-Quantum Cryptography
As computing technology evolves, it’s inevitable that somebody will break algorithms like AES and RSA at some stage. The significant computing power required to brute force these algorithms within a realistic time frame remains a long way off. However, experts predict that with the dawn of commercially available quantum computers forecasted within the next three decades, the current encryption and signature methods will fail to protect information. Developing and testing new encryption methods based on more complex mathematical problems are underway. Governmental and industry research organisations are calling on the embedded development community to be prepared for post-quantum cryptography (PQC)by working with silicon vendors, security specialists, and partner ecosystems to achieve certification to new security standards. Despite thirty years seeming a long time to prepare, the reality is that many industrial IoT deployments made today will still be in use when access to quantum computing becomes available.
Security for Embedded Systems
Securing an embedded system from attack is paramount. Connected devices are all around our homes, offices, and factories—even in our vehicles. Each device offers a pathway to other systems, providing an expansive attack surface to any adversary wishing to disrupt or take control of a system or network.
This short article has highlighted some potential attack vectors and methods which hackers may employ to compromise an IoT/IIoT device. The article also briefly explained asymmetric and symmetric encryption methods and hashing techniques.