Unfortunately, a number of these choices limit the anti-counterfeiting protection that engineers had hoped to gain, in particular, many systems fall victim to side-channel attacks. With this in mind, what are the key factors that design engineers should consider in their decision making process.
Anti-counterfeiting (ACF) ICs fall into two categories. The first – state machine designs – have fixed functionality, fundamentally performing a single task and turning challenges into responses in a secure manner. The second, more advanced category, is software programmable devices, such as a trusted platform module (TPM). These typically include a wealth of different security protocols.
Both state machine and programmable authentication ICs at their core participate in a challenge/response protocol (e.g., protocols similar to CHAP) to provide authentication. For a challenge, a large series of random data is sent by the verifier host. The ACF IC then performs cryptographic operations on that data, usually encrypting it using the secret seed data stored within the ACF chip. The encrypted response output is then returned to the verifier host, which cryptographically confirms that the ACF knows the appropriate secret, and thus verifying that it is authentic.
Above: Inside an IC
However, not all ACF ICs are created equal. The savviest design engineers recognise the need to audit this sort of system in order to determine the sometimes subtle, but critical variances that make the difference between a secure design and an unacceptable risk. Critical considerations include:
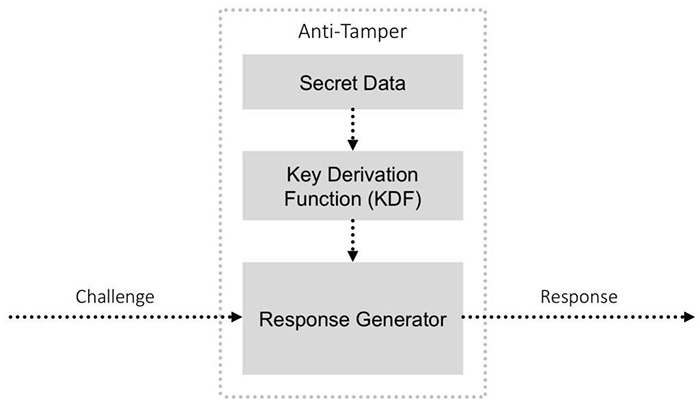
1. How is the secret data stored in the device? How well protected is it? First, look at the exact type of non-volatile memory (NVM) used, and how resilient it is in the face of non-invasive, semi-invasive, and fully invasive attacks on the chip. How a vendor chooses to store the secret data is critical.
One-time programmable (OTP) memory is generally agreed to be more secure than charge-based memory, such as embedded flash and electrically erasable programmable read-only memory (EEPROM). While each is vulnerable to a sustained invasive attack, charge-based memory is more easily reverse-engineered by semi-invasive scanning electron microscope techniques.
2. Which key derivation function (KDF) is used? How is the secret data converted into a key used to encrypt incoming challenges? Next, evaluate what KDF is used in the chip. The KDF usually takes data stored within the NVM and processes this to become the secret key. Using a proof-of-work (PoW) function to derive this key from the secret data is considered best practice. A PoW algorithm is relatively demanding, requiring clock rates and wide data paths that cannot be effectively emulated in the low-cost microcontrollers typically used for counterfeiting.
Having a KDF with a PoW function assures the system designer that every time authentication is performed on that ACF IC, the chip not only verifies that it knows the secret key but that it also can perform the KDF algorithm. This is in effect a two-factor authentication and specifically prevents an adversary from deploying a low-cost processor that has simply been programmed with stolen secret data.
3. What is the encryption algorithm? How is it implemented? How susceptible is the processing to fault-injection attacks and DPA attacks? Next, assess the encryption engine used to translate the challenge into a response. Most security chipmakers use Elliptic Curve Cryptography (ECC), while other chips use the Secure Hash Algorithm (SHA-2 and SHA-3) or the Advanced Encryption Standard (AES). There are a number of ways to combine challenges and derived keys to elicit a response, so that an adversary is unable to reverse-engineer the secret key based on challenge/response data.
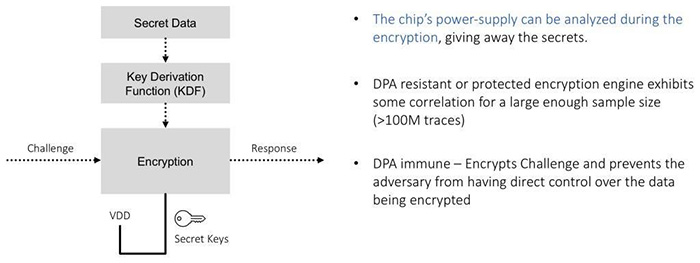
DPA attacks (a type of side-channel attack), are a critical factor to consider along with the type of encryption. A DPA attack is when a counterfeit chipmaker or adversary tracks an authentic chip’s power supply usage while it’s performing cryptographic actions. By recording and analysing those waveforms, with knowledge of the encryption algorithm and processor used, it is possible to map-out parts of the encryption key. In most cases, that’s enough information to recover the secret key value from the security chip.
All encryption methods are vulnerable to combinations of Differential Power Analysis (DPA) issues. Regardless of the algorithm you use, they all leak some information related to the secret key when deriving the response to a challenge.
DPA is conducted without incurring the expense of gaining access to the die required for invasive attacks. Therefore, the type of memory storing secret data in the chip and anti-tamper protection can be rendered irrelevant. If the encryption algorithm isn’t DPA-protected, a determined adversary can recover secret keys via a DPA attack.
 Above: DPA-resistant vs DPA-immune
Above: DPA-resistant vs DPA-immune
Focus is on selecting a device with an algorithm implemented to compute challenge responses in a way that is DPA-immune. With DPA-immune implementations, an attacker can collect hundreds of millions of power supply traces from a security chip for no gain.
Be sure to differentiate between DPA-resistant or -protected and DPA-immune protocols. DPA resistent implementations still exhibit key correlation for large enough samples (>100M traces) of power supply traces. DPA immune encryption engines use additional techniques such as preventing the attacker from having direct control over challenge data, thus frustrating analysis.
4. What are the overall anti-tampering features of the chip? Lastly, ensure that there is an anti-tampering capability in the ACF device. This capability reduces the likelihood of an adversary successfully gaining access to probe an intact die and electrically probe or otherwise analyse the device.
A key challenge for design engineers in conducting the above analysis is that most information about a device’s anti-tamper technology is not publicly available. This is because a chipmaker’s techniques are exclusive to them and that this information would be of high value to adversaries. In most cases, a Non-Disclosure Agreement (NDA) can be used to obtain information on how this critical layer of security is implemented, before making design decisions. It is worth having an NDA in place as understanding exactly what the ACF IC will do with its secret data, in case of physical tampering, is vital to developing a secure design.
Final thoughts – ACF should be a priority, not an afterthought: Adopting anti-counterfeiting technologies must be considered as a priority, not an afterthought, otherwise entire industries, and in some cases human lives, could be jeopardised. With adversaries becoming more sophisticated and motivated, unless there are better decisions made when it comes to system security, we expect to see more counterfeit products enter the market.