This is what Imperva recently witnessed firsthand while mitigating a wave of send-to-a-friend spam attacks with an interesting thematic twist.
Form-filler bots and send-to-a-friend spam
Send-to-a-friend (a.k.a. share-with-a-friend) is a social sharing module commonly found on commercial websites. As the name suggests, their purpose is to help users email the details of a product/service to their friends. To make sharing easy, the email is sent directly from the website itself, typically by filling in a short online form.
What many fail to consider, however, is that these modules tend to draw the interest of spammers.
For them hijacking such modules has several benefits, including:
- IP obfuscation – Email services rely on IP reputation for spam filtering. Sending messages from a server that has no prior record of malicious activity is a way of bypassing such filters. It’s also a way of avoiding the risk of being tracked by law enforcement.
- Spam link obfuscation – Send-to-a-friend emails are issued by legitimate senders and feature design templates and details of real offerings. Spam links in such emails are more likely to be clicked by their recipients.
- No operational costs – Sending emails en masse is expensive. Abusing third-party email services is a good way to avoid these high costs.
Motivated by the aforementioned, spammers will actively search for sites with send-to-a-friend functions that can be exploited for their own purposes.
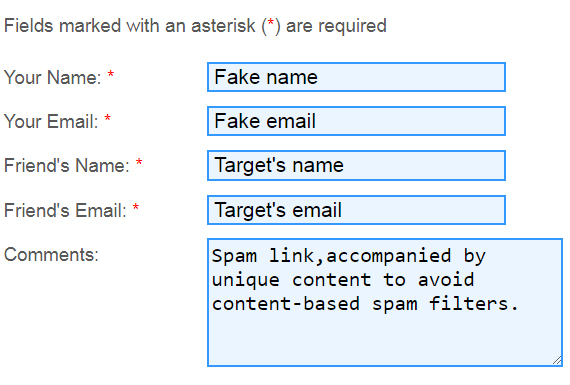
Once a target is found, spammers will unleash a host of form-filler bots on the send-to-a-friend form, using them to send thousands of emails with embedded malicious links.
It was while monitoring the activity of such bots that we saw spammers turning to the dark side of the Force.
A page from a Star Wars Novel
We first felt a ‘disturbance’ in mid-October, when several of our customers were bombarded with suspicious WinHTTP POST requests from yet-unidentified bots.
The high rate of these requests, in addition to the considerable number of targets, caught our attention. Even more so, the similarities between the attacks showed them all to be part of a larger coordinated assault.
During the first week of the assault, from 10th to 16th October, 33 unrelated domains on our network were hit by over 275,000 attack requests. A week later, the number of targets had increased to 60, and the volume of the attack had almost tripled – reaching a total of over a million requests.
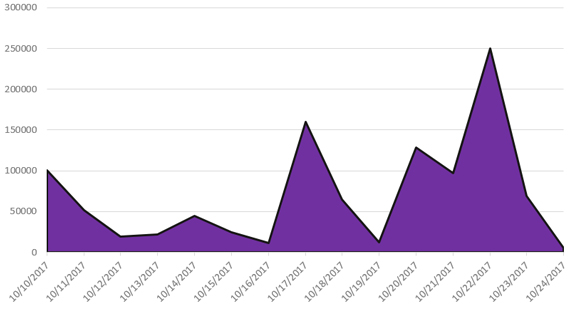
Figure 2. Number of attacks requests blocked per day
The assault was carried out via a botnet, which enabled the attackers to spread the request output. This was likely an attempt to avoid rate-limiting mechanisms, which are commonly used to protect online forms. In total, in the first two weeks of the assault, we were able to identify 6,915 devices participating in the attacks, 98.9% of which were located in China.
The thing that truly piqued our interest, however, was the content that the bots were stuffing into the comment section of the send-to-a-friend emails.
There, alongside a link or two to a sleazy-looking website offering a selection of gambling apps, Imperva found snippets of text that didn’t look like the randomised content we’re used to seeing in spam emails.
One swift Google search later and they discovered that these snippets were in fact quotes taken from Star Wars novels, chopped up into incomprehensive chunks and used for the purpose of peddling mobile slots.
Here, for example, is a POST request crafted to inject spam links with an excerpt from Path of Destruction, a Star War Legends novel.
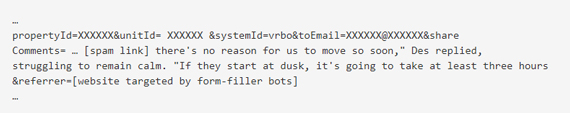

At present, it can only be speculated about the reasons for the unwarranted quotes from Star Wars literature.
Most likely, however, the spammers were trying to add some uniqueness to their emails, and further hinder detection by filtering mechanisms scanning for content patterns. In the process of doing so, the culprits probably also decided to pay homage to one of their passions.
One way or another, much like the rest of us, these scruffy-looking nerf herders have Star Wars on their mind.
Pass on what you have learnt
As these very words are typed, the aforementioned attacks continue to target our customers. A sampling of some of the more recent attack requests shows that attackers have now moved away from using content from Star Wars novels and expanded their range to include quotes from ‘Jane Eyre’ and the works of Edgar Allan Poe.
While our customers have nothing to worry about, the scope of the attack makes us believe that many other sites are also being targeted outside of our deflector shields.
For these unprotected targets, the repercussions of an attack could be dire, as they are at risk of being blacklisted by major email service providers. This can have a severe impact on the day-to-day of an online business – not only hampering email marketing campaigns but also preventing any sort of reliable email communication with customers.
For an online service that often relies on emails for billing, support and other mission-crucial activities, this immediately translates into a lot of overhead. Not to mention, plenty of headaches for everyone involved.
To stay ahead of the attackers, developers and operators need to recognise the security risks that come with having an email sharing option on their service and take steps to prevent it from being abused by form-filler bots.
At a minimum, they should include a rate-limiting mechanism that will prevent an IP address from issuing unreasonable numbers of requests over a specific period of time. Other DIY solutions are to have all users fill in CAPTCHAs and to enforce registration as a prerequisite to sending out an email message.
That said, our experience shows that persistent attackers will eventually circumvent any, and all of these halfway methods. Your best bet, as you would expect, is to go with a purpose-made bot filtering solution, or as Master Yoda would say: “Do or do not, there is no try”.







