The smart factory, that is autonomously enhancing itself, has yet to become reality. However, manufacturers of industrial components and devices have to prepare manufacturing equipment to make this vision become a reality. This is why functionalities that allow predictive maintenance, remote control and remote software updates are being included already. As they are all usually connected through the internet, we are hence talking about the IIoT – Industrial Internet of Things.
However, connectivity also comes with new security challenges: malware, manipulation, sabotage, faulty firmware updates and counterfeit components are examples of digital threats that can bring entire production lines to a halt. In addition, safeguarding intellectual property (IP) and sensitive information requires tailor-made solutions.
Security measures that are based on software alone do not generally provide sufficient protection against a large number of increasing and upcoming attacks. Cryptographic keys (secrets) – used for example to prove the digital identity of a device – and sensitive information, are best protected by a strong foundation based on hardware-based security. Security which is based on discrete security chips enables higher security levels of industrial devices and networks to be achieved, and also helps to shorten time to market and reduce development costs of secured industrial applications.
IEC 62443: A standard for industrial cyber security
The IIoT or Industry 4.0 and smart factories are based on interconnection and integration at all network levels – from IT to OT network and connected machines (M2M). Yet this increased connectivity leads to vulnerabilities for attacks especially from the ‘outside’ through using remote accessibility. Companies must therefore be prepared against cyber threats in order to prevent equipment damage or down-time.
Industrial control systems have experienced a significant increase in cyber attacks over the last decade. The industry has responded to cyber security threats by creating standards to assist end users, plant manufacturers and integrators through the process of securing industrial control systems and networks. IEC 62443 has been developed by both the ISA99 and IEC committees as an international industrial security standard with the aim to improve the protection, availability, integrity, and confidentiality of data for components or systems used in industrial automation and control.
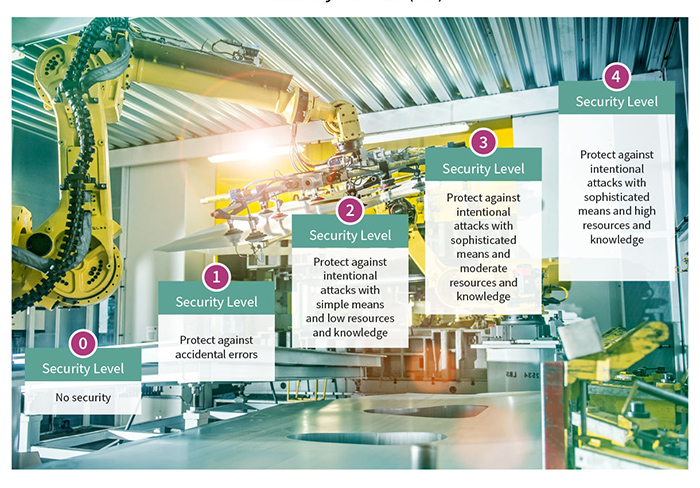
Above: Figure 1. Standards like IEC 62443 and JEDEC JESD47 define the usage of components in secured industrial applications
IEC 62443 defines five security levels: from SL 0 (no security) to SL 4 (resistant against nation-state attacks). For the higher security levels (i.e. level 3 and 4) of IEC 62443, hardware-based security is a requirement to protect the device authenticators, the private keys and also critical symmetric keys to name some examples. The advantage of storing critical secrets and data within a discrete hardware chip comes with enhanced protection as a dedicated security chip is hardened against logical as well as physical attacks.
Whereas with software only methods the barriers for logical attacks are much lower. Attackers could analyse the code to find vulnerabilities and develop exploits that undermine security and may, for example, be used to extract secrets. Those ‘stolen secrets’ could then be used to impersonate or copy the device. This is critical, as it is very hard to verify whether something is the original device or a device that has the stolen and copied keys. Think of the use case of predictive maintenance, where first of all huge amounts of data are being analysed to derive the indicators to identify the failure of a device before it happens. Data that is not derived from an original device cannot be trusted and consequently must not be used within the analysis.
The IEC 62443-4-1 standard has responded to this scenario – product suppliers who use externally provided components such as security chips must employ a process to identify and manage the security risks of those components. Furthermore, they must be able to identify the degree of security verification and validation performed on the component.
Certified security chips like the OPTIGA Trusted Platform Module (TPM) from Infineon support those requirements. They are evaluated by independent security testing laboratories according to the Common Criteria (CC) protection profile for IT products and certified by authorities like the Federal Office for Information Security. The certificates are published on the Common Criteria website and prove the conformity with the requirements of the security profile.
Use cases for securing industrial networks
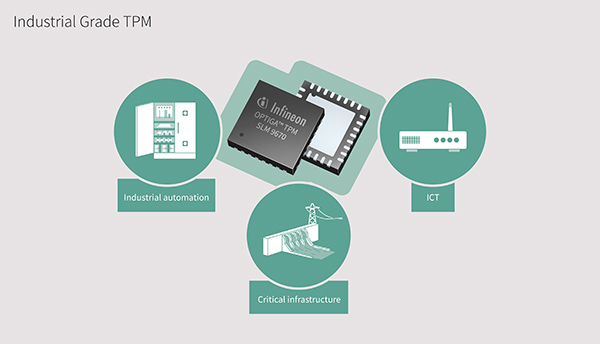
Security measures have to cover the complete industrial infrastructure including the components (e.g. PLCs, IPCs, RTU, HMI), gateways, routers and servers. What are the typical use cases in the industrial infrastructure which should be based on hardware-based security? Predictive and remote maintenance with related monitoring, diagnosis and services is one important topic. Other relevant and critical applications in smart factories are counterfeit detection, protection of IP and software upgrades, and so on.
In order to implement predictive maintenance and remote control in a highly secured manner, strong device authentication is key. Secured digital identities of machines are the basis for protecting data exchange and the establishment of secured communication channels, e.g. from the industrial controls to the cloud.
Consequently, the underlying secret keys must be protected properly during the whole lifecycle of the product. This can be done most effectively using hardware-based security, comparable with a vault.
Above: Figure 2. The OPTIGA TPM SLM 9670 protects the integrity and identity of industrial PCs, servers, industrial controllers or edge gateways. It controls access to sensitive data in key positions in a connected, automated factory as well as at the interface to the cloud
Besides faking the device ID to access industrial networks, common attack scenarios also include eavesdropping data and commands as well as active attacks on networks that try to inject data packets and disrupt the operations. To recognise these kind of attacks, there is a need for authentication with tamper-resistant security chips. They allow clear identification of the device and the data source.
Another important topic is secured software updates that are used to close vulnerabilities or to add new functionalities to the device. There is the need to identify the device and to check that it has the proper license to download the new software. The device must be protected against attackers using the software update mechanism to install their own malware. Furthermore, it is important to be able to verify the authenticity of the software update source and to make sure that the code has not been manipulated. Finally, software updates should be encrypted. Security chips play a central role in this scenario – they protect the cryptographic keys required to decrypt the update package.
Trusted computing in industrial applications
A Trusted Platform Module (TPM) is the standardised and certified foundation for secured components and computing platforms. The TPM protects secrets such as keys and other security critical data in a discrete security chip (i.e. separated from the main CPU) in order to take over critical security operations within its own, protected resources. The TPM can communicate with the main CPU – the processor on which the application is running. The hardware of the TPM is a security microcontroller with its own CPU, memory and crypto-coprocessors taking over security critical operations and storing security critical data (i.e. keys). Logical attacks commonly exploit software vulnerabilities to manipulate, steal or copy critical keys. TPMs are specifically designed to be hardened against such attacks and therefore protect keys and other security critical data both against logical and physical attacks.
Furthermore, device manufacturers can benefit from reduced cost and effort when they use security chips. With a pre-provisioned security chip, there is no need of setting up protected and audited manufacturing environments or changing the manufacturing processes to insert device ID and secret keys. Device manufacturers can rely on the TPM as protected key storage and do not need to develop their own security products. Thus, time and cost is saved.
Complete and dedicated family
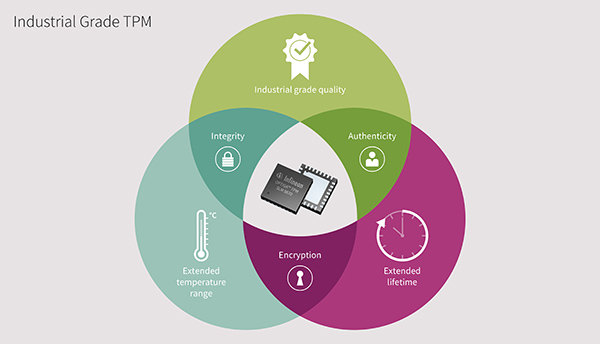
Infineon’s comprehensive OPTIGA family offers different security chips providing core functions to secure devices and embedded systems in a range of products from one-way authentication up to a flexible, fully fledged standardised security building block (TPM), optimised for different market segments. The OPTIGA TPM SLM 9670 is the latest addition specifically designed for industrial applications.
The OPTIGA TPM SLM 9670 security chip meets the requirements of industrial applications covering the complete industrial infrastructure, such as components (i.e. PLCs, IPCs), HMI (Human Machine Interface), gateways/routers and servers. This certified and standardised security chip protects the secrets that are used for a strong digital device ID and device authentication and enables the verification of data source as well as the clear assignment of data to the right machine. The TPM also includes functionalities to protect the confidentiality of data and IP. This ready-to-use security building block is equipped with dedicated and optimised functions to protect industrial devices and systems, including software features and updates.
Above: Figure 3. OPTIGA TPM SLM 9670 is optimised for industrial applications
To meet industrial requirements, the new SLM 9670 provides an extended temperature range (-40°C to +105°C), extended lifetime (20 years), extended product availability for industrial development cycles, enhanced reliability and industrial quality grade. As with the other OPTIGA TPM family members, it is based on a tamper-resistant security microcontroller that leverages advanced hardware security technology. Pushing beyond the qualifications performed for standard
TPMs, the SLM 9670 is qualified according to JEDEC JESD47, the standard for industrial applications.
In addition, the OPTIGA SLM 9670 hosts essential cryptographic operations including the generation and verification of keys and signatures with cryptographic algorithms like RSA-2048, ECC-256 or SHA-256.
Availability
TPMs are based on an open, vendor-neutral global industrial standard created by the Trusted Computing Group (TCG). Major operating systems such as Microsoft Windows 10, LINUX or VxWorks therefore support OPTIGA TPM with plug-and-play usability. Additionally, a wide range of software including libraries and applications is available both as open source as well as from commercial security experts and industry leaders.
The OPTIGA SLM 9670 is fully compliant to the TPM 2.0 standard issued by the TCG. Previous designs with the OPTIGA TPM SLB 9670 (TPM 2.0) can easily be retrofitted for the OPTIGA SLM 9670. Built-in TPM features such as a true random number generator (TRNG) enhance the security level of the system. Advanced hardware security technology, which includes internal memory and bus encryption as well as shielding, in addition to security measures such as sensors, provide robust protection against physical and logical attacks.
For fast and easy evaluation and development, Infineon offers a variety of boards. The Iridium boards are compatible with Raspberry Pi and equipped with a variety of OPTIGA TPMs including one with the SLM 9670.





