Growing risk
Connected devices are being adopted at breakneck speed. According to Statista, the average number of devices and connections per person globally was 2.4, with this forecast to rise to 3.6 in 2023. The greatest growth is expected to come from North America and Western Europe where each person will have 13.4 and 9.4 connected devices, respectively. This creates more opportunities for cyber criminals to gain access to your personal world and we are already seeing a huge rise in attacks. This is particularly true for smaller, embedded devices, which are often overlooked, making them an easy target. Adopting a security protocol for these devices is an essential step in securing the supply chain and avoiding more critical attacks.
Humans can check faces, voices, or mannerisms to decide whether people are who they say they are. When it comes to machines asking an identifying question and trusting the answer, it is vital to establish meaningful and trusted communications. Machines must have unique identities and be able to prove and identify themselves. This means there needs to be a way to check the legitimacy of those identities with an external reference through a chain of trusting relationships – a root of trust.
What is a Root of Trust?
A Root of Trust (RoT) is the foundation on which all secure operations of a computing system depend. Essentially it is a set of functions that can always be trusted within a cryptographic system, and which can be installed by embedded system manufacturers within a device.
RoTs are a fundamental part of trusted computing, as they support the accurate establishment of the identity of a device within an IoT ecosystem. This is vital so that each device can demonstrate that is has not been tampered with. This process is referred to as Measurement and Attestation (M&A). M&A mechanisms have already been developed for PC and server platforms but porting these technologies directly on mobile and resource-limited devices does not satisfy their performance constraints and requirements. There are ongoing research efforts to create mobile-efficient integrity M&A mechanisms and Trusted Computing Group has written specifications for the industry to follow to ensure all devices collectively work and talk coherently to each other.
M&A are critical technologies for evaluating the trustworthiness of software platforms. To best support these technologies, next-generation operating systems must provide a centralised service for securely selecting, collecting, and evaluating integrity measurements. Centralising M&A avoids duplication, minimises security risks to the system, and ensures correct administration of integrity policies and systems.
Security as standard
The Trusted Platform Module (TPM) provides a standardised hardware RoT to help measure integrity and provide health checks and authentication services within a device. The TPM is a computer chip designed to provide hardware-based, security-related functions and is the standard hardware that can provide RoT with integrity measurements, health checks and authentication services to protect embedded systems.
Depending on the requirements of each unique system, the chip can be implemented at different security levels and is equipped to protect even against the most sophisticated attacks. With the main objective always being the ability to determine the devices integrity, TPM capabilities can be used to prevent hackers from being able to replace code on devices and access encrypted data by isolating keys. This ensures data remains protected from unauthorised users.
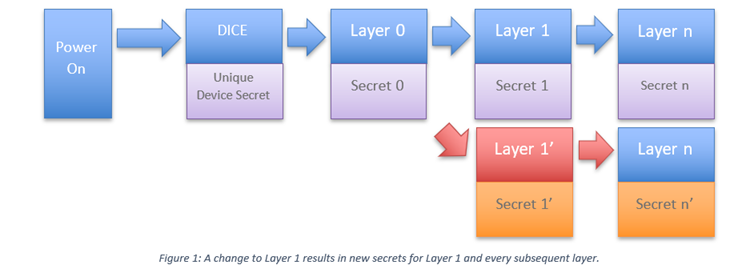
Device Identifier Composition Engine (DICE) based architecture provides another alternative route to successfully confirming trustworthiness. DICE capabilities can help perform attestation, authentication, and certification of software. DICE uses a combination of a small hardware engine and security code embedded in boot code and later software layers to provide device identity, integrity reporting and data protection capabilities. For low-cost, low power endpoints, DICE architecture provides cryptographically strong device identities which forms the foundation for attestation for software updates, patches and so on.
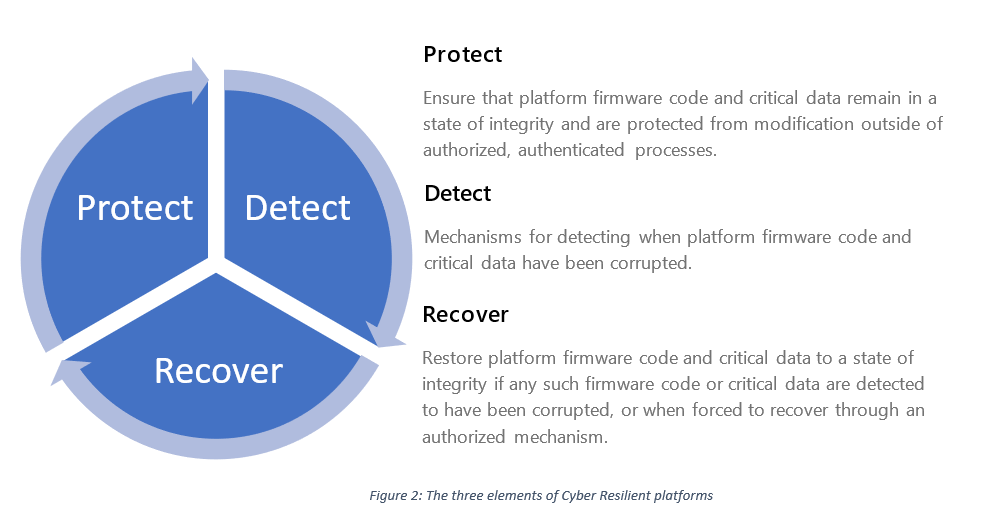
As security standards become a priority for manufacturers, engineers should also look to resilience technologies and build on the protection offered by TPM and/ or DICE on IoT and other systems. As consumer IoT continues to rapidly outnumber people it is key to ensure their devices have security capabilities which have an automatic way to recover a device to a trusted step in an automated way and without the need of manual interference. Resilience encompasses better protection, and detection of compromises with a reliable recovery to a trusted state.
Security by design
Unfortunately, there are no easy answers to the question of how to build a strong RoT for an organisation’s cryptographic infrastructure. In some cases, a combination of solutions is needed. Despite this, it is imperative that organisations rise to the challenge and ensure that the cryptographic skyscraper that they build stands on strong foundations.
In conclusion, a ‘Zero Trust’ approach to a system is needed whereby the integrity of each device and its movement of data can be determined. Adopting trusted computing standards can help create the pervasive security validation needed in this kind of approach. With the complexity of devices, environments, applications and use cases, there is not a one-size fits all approach when it comes to cybersecurity, rather a diverse approach is needed to address unique needs.
The Trusted Computing Group (TCG) has developed a wealth of security standards and trusted computing technologies which address the security challenges of today and the future. Utilising RoT as a foundation for the security of every device, TCG ensures that all safeguarding needs from the smallest devices to Industrial IoT (IIoT) are met.