Outlining why security must be a foundational enabler for IoT
Vinod Vasudevan, Co-Founder and CTO of Paladion, had the opportunity to participate in a panel discussion on the Internet of Things (IOT) and Cybersecurity at CyberSEED. CyberSEED being a platform pioneered by Comcast Center of Excellence for Security Innovation at the University of Connecticut to bring together cybersecurity leaders, business leaders, government and universities.
In this piece, Vasudevan will share the key ideas, discussed in the panel on IOT security and the broader linkage to cybersecurity initiatives.
The arrival of the IOT era
IOT is a revolution in the making. It is possibly the only technology that has enterprise, consumer, and industrial use cases. The industrial use cases are also called Operational Technology or Industrial Internet of Things. Now use cases are growing in number by the day, increasing their possibility of influencing our lives in the years to come.
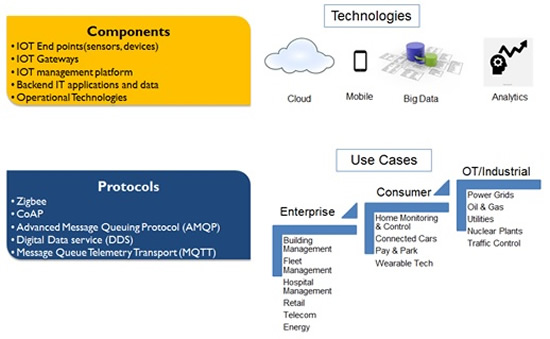
At the consumer level, the adoption of IOT for areas including home monitoring & control, wearable tech, and connected cars has already started. At the enterprise level, adoption is active for building management, fleet management, hospital management, retail, telecom, and energy sectors. Operational technology has been long adopted by power grids, oil and gas, utilities, nuclear plants and traffic control. With increased connectivity between SCADA networks and IT in these organisations, industrial internet is becoming a reality.
The risks of IOT implementations
Despite the huge positive impact IOT has over the lives of individuals, employees and customers, the risks which accompany this technology can act as a significant hurdle in adoption. Security issues in IOT are especially a concern as they have the power to cause physical destruction, harm lives and also cause financial impact.
IOT risk factor is unique since it brings together many leading edge technologies including cloud, mobility, and big data in addition to IOT sensors, gateways, and management platforms. IOT security therefore includes risk areas that cybersecurity industry is still learning to resolve including cloud & mobility. IOT security also includes unknown risk areas in the form of IOT sensors, protocols, gateways, and management platforms. Add to this the regular IT systems that IOT platforms integrate with and you get a complex mix of risk areas that should be protected.
If we plot these areas as a combination of attacks (known/unknown) and threat actors/attackers (known/unknown), we can quickly see that there are some key areas where we are fully in the red and some where we have an understanding of attacks & attackers.
Here is a quick look at a set of illustrative risks in the IOT spectrum:
- There are many IOT protocols in the market today including Zigbee, CoAP, Advanced Message Queuing Protocol (AMQP), Digital Data service (DDS), and Message Queue Telemetry Transport (MQTT). These protocols are either new or derived for IOT from an earlier version used for generic purposes. As a result, they are vulnerable unless special effort is taken to secure them. As an example, Zigbee is a common IOT protocol now though it was originally conceived for low power wireless use.
- IOT management platforms have web interfaces and related protocols enabled. Therefore, they are exposed to common web application attacks, including SQL injection, cross site scripting, parameter manipulation. The impact of exploiting such weaknesses in an IOT management platform is high since it can be used to subvert millions of sensors for a malicious purpose.
- IOT management platforms are also hosted in cloud infrastructures. Any adversary who knows how to exploit the cloud on which IOT is hosted can get direct control of IOT management interface. The thousands of consumers who are subscribed to an IOT provider for home monitoring and control can be subject to burglary if the cloud on which this provider is hosted gets compromised.
- Mobile devices also run software that enables mobile to function as an IOT sensor. Mobile devices can also run apps which interact with other IOT sensors. However, mobile device compromises can also lead to breach of IOT components on mobile.
IOT will further complicate the cybersecurity challenges that we already have on hand, including the challenge of detecting unknown attacks.
In this context, IOT security means securing the different components on which the IOT solution is built on. This includes the cloud that it leverages, the IOT protocols which are part of the solution, and the related IT infrastructure and mobile devices.
Overall, it will take time for the ecosystem to reach maturity in terms of products, protocols and industry standards. Even at a mature stage, many of the risks discussed here will need to be managed with diligence by the enterprise rolling out IOT projects. On a pragmatic note, Vinod suggests that the following top three activities be carried out by any enterprise rolling out IOT solutions to achieve meaningful security:
- Build security into IOT architecture with relevant components – Doing so will provide around the box security till the time IOT protocols can be secure by design. This requires adhering to fundamentals including authentication, access control, and encryption.
- Build monitoring controls at different levels –This step covers IOT gateways, IOT management platform, IT infrastructure, and cloud monitoring to ensure that attacks are caught early.
- Detailed security assessment and penetration testing – These tests are imperative for secured IOT infrastructure before roll out and on a periodic basis.


