Facing the cyber security challenge
The cyber security landscape is changing and there are a number of challenges emerging for industry and businesses, particularly from an IoT perspective. Speaking at the Drives & Controls show in Birmingham, Andrew Johnston, a cyber security specialist with Cisco, highlighted the concerns.
He started off with an alarming quote from former Cisco CEO John Chambers, who made a statement to the industry around two years ago in which he warned that. “There are two types of company: Those that have been hacked and those that just don’t know it yet.”
A statement such as that from a company such as Cisco, which has such experience in the cyber security arena, does on the face of it make for grim reading - particularly when you observe the development of the hacking landscape over the last two decades.
A growth industry
Cisco has also coined the phrase ‘The industrialisation of hacking’ (see below) and this looks at the development of hacking since the low sophistication of phishing hacks in the mid-1990s, the point in the mid-2000s where hacking really became a global industry and on to the complex and sophisticated landscape we have today, which involves nation state attacks targeting critical infrastructure in other countries.
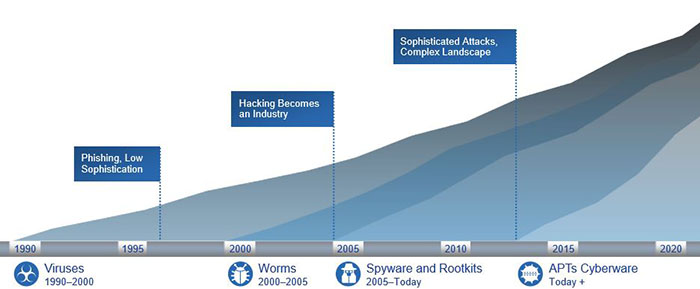
Despite this a number of security myths have taken hold among some organisations - the most common of which are: There is an air gap between the hackers and my infrastructure so the threat is fairly minimal (this is an erroneous belief, highlighted by the fact that a simple Rubber Ducky USB can be purchase over the internet for as little as $50.00, giving hackers a way in); I am achieving security through obscurity (the belief that a system of any sort can be secure so long as nobody outside of its implementation group is allowed to find out anything about its internal mechanisms.); and the view that even if my infrastructure is hacked it will have limited impact.
The belief in these cyber security myths are even more disconcerting when the prevalence of targeted attacks are taken into account. In 2016 there were a total of 290 targeted cyber attacks around the world (compared to 74 in 2012 – which highlights the growth of hacking), and no sector has been left unscathed - from communications and critical manufacturing to energy and water providers. Hackers are going after everyone, irrespective of the size of the organisation, or which industry they happen to be in, and unfortunately the black hat hackers and the dark web are making things easier.
The motivations of these hackers are quite simple – it could be to do harm such as a nation state wanting to take over another’s infrastructure; it could be for financial rewards or it could be as basic as hackers having ‘fun’. Unfortunately for Cisco and its customers the hackers have the advantage.
The unpalatable reality is that a hacker could quite easily launch an attack on your infrastructure, plant something, and that attack could lay dormant for some time until a particular vulnerability is opened up and that attack can take place - with devastating effects.
As a consequence cyber attacks are more damaging than ever and the risk is increasing. This is due to automation systems increasingly being connected to enterprise IT systems; enhanced third party access for greater troubleshooting and optimisation; the move from niche and proprietary systems to ubiquitous IP/Ethernet; a more ready supply of hacking tools and the fact that ICS protocols are inherently insecure.
Case examples
This is not just scaremongering. There have been some significant attacks on a variety of installations over the past few years (some more high profile than others), which highlight the extent of the issue. A select few are outlined here and range in cost from $1.9m to $65m:
Destroyed uranium centrifuges - 2010: Iran's nuclear programme was threatened by a powerful virus distributed through the internet. The attacker managed to access the system via a USB key on an air conditioning device. The attacker managed to access the centrifuges and the programmable logic controllers (PLCs), which enabled them to blow the centrifuges. This particular attack put the Iranian uranium programme back three to four years. It took them that long to work out where the attack came from and subsequently fix the problem.
Ruptured oil pipeline – 2008: The August 2008 Baku-Tbilisi-Ceyhan (BTC) oil pipeline explosion in Refahiye, eastern Turkey, was ruled at the time to be an accident resulting from a mechanical failure, which itself was a result of an oversight by Turkish government supervisors. However, western intelligence services concluded that the explosion was the result of a cyber attack. Hackers apparently infiltrated the pipeline’s surveillance systems and valve stations, and super-pressurised the crude oil in the pipeline, causing the explosion.
Manipulated steel mill equipment – 2014: A blast furnace at a German steel mill suffered "massive damage" following a cyber attack on the plant's network. Attackers used booby-trapped emails to steal logins that gave them access to the mill's control systems. This led to parts of the plant failing and meant a blast furnace could not be shut down as normal. The attackers used both targeted emails and social engineering techniques to infiltrate the plant. In particular, the attackers used a spear phishing campaign aimed at particular individuals in the company to trick people into opening messages that sought and grabbed login names and passwords.
Regional power outages – 2016: A power cut that hit part of the Ukrainian capital, Kiev, was judged to be a cyber attack by researchers investigating the incident. The blackout lasted just over an hour and started just before midnight on 17th December 2016. The cyber security company, Information Systems Security Partners (ISSP), linked the incident to a hack and blackout in 2015 that affected 225,000 people. It also said a series of other recent attacks in Ukraine were connected. The 2016 power cut had amounted to a loss of about one-fifth of Kiev’s power consumption at that time of night.
Back to basics
It’s vital to get the basics right when it comes to security, and to have defence in depth. It’s something that can’t be fixed by purely throwing a lot of technology at the problem.
The modern industrial environment has thrown operational technology and information technology together. The two have very different outlooks, but security must have a two pronged approach between technical and non-technical departments and personnel. Technical controls such as Firewalls, Group Policy Objects, Layer 3 ACLs and NACs must combine with a strong company ethos, rules for certain environments, policy and procedure, risk management, best practice, vigilance and attention to detail.
There’s an old joke where two men are being chased by a bear, and as the first man starts to break into a sprint the second man exclaims: “What are you running for? You can’t outrun a bear!” To which the first man replies: “I don’t have to outrun the bear, I only have to outrun you!”
As such it’s important to remember that technology is only as secure as its weakest link so it’s important that employee best practice is enforced - there is no point in having a whole host of IT security in place if an employee then writes his or her password down on a post-it note and places it next to their terminal.
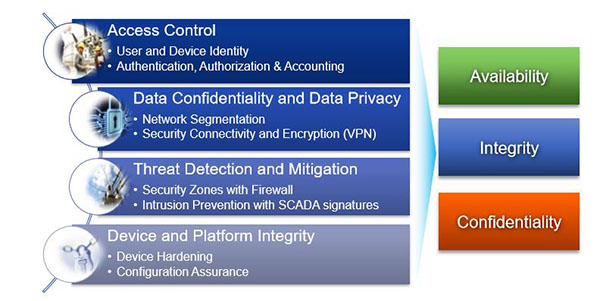
Cisco has established a number of industrial security techniques to assist companies with achieving their security goals. These can be seen below. In addition, The National Cyber Security Centre has recently published 10 steps to cyber security to help organisations get up to speed with their security challenges and frameworks.
Conclusion
So, cyber attacks are increasing rapidly and that is not likely to stop any time soon. The truth is that the odds are against you. However, if you assume that your organisation will incur a breach it does change the thinking and ethos of the company from essentially a reactive standpoint to a proactive one.
The potential consequences of an attacks have been outlined here, so it’s important to have a comprehensive security strategy in place but as we’ve also covered that’s not just about products – it’s also a mix of people and technology spanning operational technology and information technology to achieve an integrated approach to your cyber security.


