Defending the IIoT
By creating a world in which physical objects seamlessly integrate into the information network, transferring data between themselves and the cloud, the IIoT is transforming everything from wind turbines and factory automation to critical infrastructure. However, with this smart, connected world comes an increased and very real threat of cyber attacks. Josef Haid of Infineon Technologies explains.
While the need to build defences to such attacks is understood, organisations may not have the tools, skill set or bandwidth to develop security measures themselves. Many, instead, seek solutions that allow appropriate security to be integrated into their systems quickly and easily, leaving them free to focus on core competencies and delivering competitive advantage. So, what are the challenges facing IIoT system architects and how can they address those challenges to provide protection while enabling innovation and minimising overheads and cost?
The risk of digital transformation
For many companies, digital transformation through IIoT implementation is seen as fundamental to delivering competitive products, optimising productivity and continuously improving business performance. Unfortunately, in addition to holding data such as passwords and intellectual property that is attractive to internet-based attackers, devices on the Industrial Internet of Things (IIoT) offer extra opportunities for disrupting business and causing damage to property and people.
Intercepting data from industrial control systems can reveal manufacturing secrets, potentially exposing a source of competitive advantage. If devices can be taken over, or cloned or spoofed, exploits can include corrupting sensor data, shutting down critical systems, and sending false control commands that can pose a serious threat to safety. Major examples include the Stuxnet attack that affected Iran’s nuclear programme and Black Energy 3 that reportedly shut down part of Ukraine’s electrical grid. There is also the work by researchers Miller and Valasek who demonstrated vulnerabilities in a car’s security architecture that allowed control of the vehicle remotely.
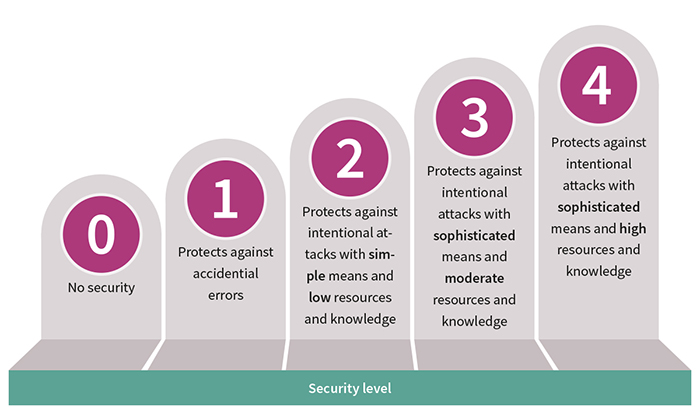
Above: Figure 1. IEC 62443 takes a pragmatic approach to the security needs of IIoT devices
Studying cyber attacks has taught the industry much about the weaknesses they exploit. As that knowledge grows, so security best practices and standards develop. These help system architects to understand the protection their assets require and techniques to resist attacks. IEC 62443, for example, founded on a risk-based analysis of potential threats, is emerging as an international standard for cyber security.
By assessing the risk to a system based on the consequences and impact of a successful attack, IEC 62443 defines five security levels (Figure 1), covering devices from those that do not require protection to those that require the highest levels of threat resistance.
Cyber security mix
Mutual authentication between end nodes, the devices they connect with (e.g. a gateway) and/or the cloud allows only genuine, uncompromised devices to communicate – as shown in Figure 2.
Without robust authentication, it may be possible to connect to, clone or load malware onto a genuine device. ‘Bad actors’ can then subsequently exploit the connection to disrupt the proper functioning of products or services, or intercept data. In addition, authentication protects providers of products or services against misuse by customers. Failures in the field can occur when non-genuine spare parts are used or counterfeit devices are inserted or an unauthorised repair is attempted. Authentication highlights rogue activity, ultimately saving the provider bearing the costs of rectification.
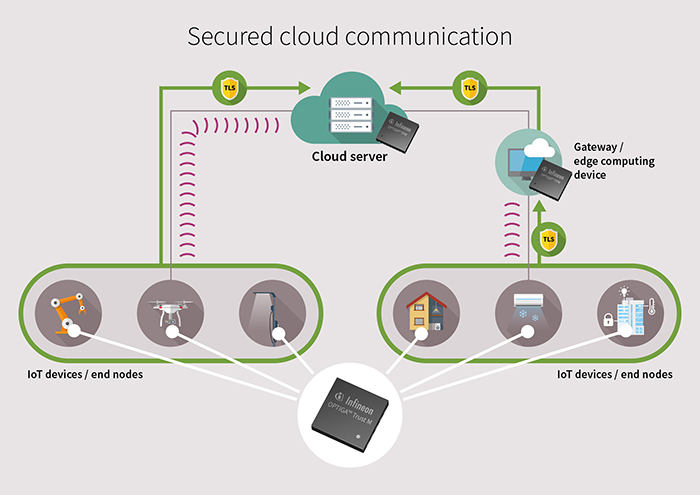
Above: Figure 2. Hardened device identities for secured connectivity to the cloud
In practice, effective cyber protection relies on several commonly employed defences as illustrated in Figure 3. These include secured communications, secured boot sequence of connected devices, and secured processes for applying firmware updates over the air (OTA).
Securing communications is important to prevent malicious agents interacting with connected devices or eavesdropping to gain intelligence or steal IP. In addition to authenticating components and personnel, and enabling connected devices to have unique credentials, encrypting exchanged data is also necessary to prevent these types of attacks. Where devices are to receive OTA (over-the-air) updates, securing this process is essential to prevent malicious software being introduced. Authentication and integrity checking is again essential, together with securing the loading mechanisms and signing and/or encrypting the code to be loaded. Secured boot processes using techniques such as code signing provide further protection for connected devices when they are most vulnerable to attack.
Securing cryptographic keys
Underlying these and the other protection measures shown in figure 2 are cryptographic keys that provide the fundamental ability to generate the challenge responses needed for authentication procedures, to digitally sign and encrypt code, and encrypt communications that can only be decrypted by authorised parties. Keeping these keys safe is critical. If they are exposed, or can be intercepted or stolen, attackers can spoof devices at will, decode secret communications, and replicate software signatures to inject malicious code. Key security is often defined in the context of ‘trust anchors’ that cover key storage, crypto operation and key management.
Protecting secret keys held in device memory using security software alone is difficult, inefficient, and impractical. The Heartbleed vulnerability in the open-source secure Sockets Layer software OpenSSL highlights the inadequacy of software-based security. Buried deep in the SSL code, a small programming error made it possible for anyone with an internet connection to examine the memory of vulnerable systems communicating over TLS/SSL and leave no evidence of a compromised system. It was spotted unintentionally yet fortunately by a software team that alerted the industry.
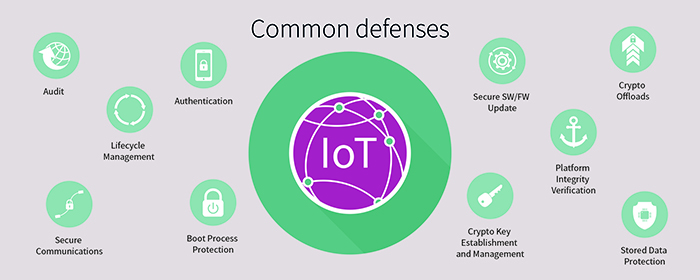
Above: Figure 3. Common cyber security defences
At the same time, it is worth noting that general purpose processors can also introduce security weaknesses, as illustrated by the Spectre, Meltdown and Foreshadow vulnerabilities discovered in some high-performance devices. Such vulnerabilities can allow malicious code to bypass checks on memory access privileges.
Secured hardware, designed specifically to isolate and store cryptographic keys and other sensitive information, can overcome weaknesses in both software-based security and general purpose processor-based systems as illustrated in Figure 4.
In the context of an IIoT device, such security hardware could be integrated either within the host system-on-chip (SoC) or separately in a dedicated secured IC. An integrated solution constrains both the secured hardware and general purpose functionality to evolve together. Separating the secured functionality in a dedicated chip gives extra flexibility for each to keep pace with developments as they occur.
Taking the full advantage of these design freedoms, standalone secured ICs can provide a high level of protection against passive and active attacks including side-channel attacks such as differential power analysis (DPA). DPA analyses the behaviour of the system when performing cryptographic calculations to find patterns that can reveal the key. Security software prevents analysis by performing many decoy calculations to mask the real calculation. Built-in DPA protection enables the dedicated secured chip to generate the desired result safely with just one calculation, more quickly and consumes less power in the process.
Dedicated security IC
Unlike software-only-based protection, secured hardware facilitates the design of chips that are highly resistant to tampering and capable of detecting attempts at accessing or corrupting stored data. Moreover, security chips that embody many years of specialised security expertise are now available ‘off-the-shelf’. Bringing up a secured system in-house from scratch can take easily two years, assuming suitable security expertise is available. If not, hiring specialist security consultants can add to the cost of the project. In contrast, security chips, combined with support from the chip vendor can deliver protection and enable compliance with current security standards.
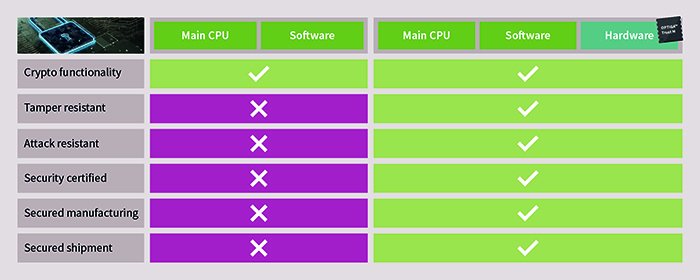
Above: Figure 4. Comparing hardware and software ‘trust anchors’
Furthermore, because chips can be programmed with customer keys at the point of manufacture, system developers do not have to invest in their own security software programming facilities and can eliminate the need to provide external contract manufacturing partners with secret keys.
On the other hand, a one-size-fits-all approach does not offer flexibility to meet the needs of the many diverse types of IIoT devices and applications cost-effectively or efficiently. Some devices may be at low risk of cyber attack and may require only device authentication with basic cryptography and keys to assist counterfeit detection. Others may require more advanced elliptic curve cryptography such as ECC-256, or may be destined for use in applications that require certification to a recognised common criteria evaluation level such as CC-EAL6+. Where cryptographically secured communication or a secured OTA update is required, a suitable security chip must support these capabilities too. Take, for example, Infineon’s OPTIGA Trust family of dedicated security ICs. This family comprises devices spanning authentication for deeply embedded systems (which can accompany MCUs in bare-metal or RTOS/proprietary-OS based systems) to the OPTIGA Trust M platform. The latter additionally supports the secured implementation of communication, data store, lifecycle management, (over-the-air) updates, platform integrity, and is ready to operate in systems running on real-time operating systems (RTOS), e.g. in FreeRTOS.
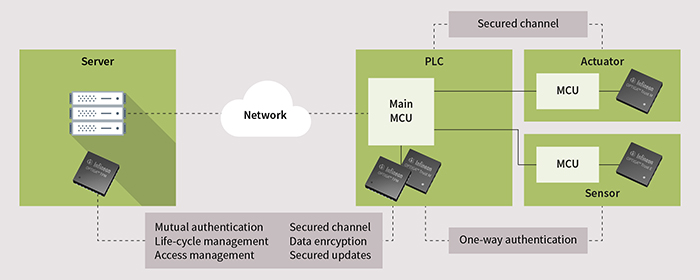
Above: Figure 5. OPTIGA Trust and TPM hardware-based security solutions provide services to protect connected devices
The highest specification device is the OPTIGA TPM Trusted Platform Module, which complies with Trusted Computing Group standards and is suitable for Windows and Linux desktop systems and servers. Figure 5 shows how embedded and TPM security ICs provide crypto-key storage and secured services to end devices and servers in an IIoT infrastructure. Open source software is available to get started with (embedded) Linux-based systems right from the beginning of the project.
Conclusion
Although digital transformation offers irresistible business benefits, the security challenges presented by the IIoT must be handled effectively. Dedicated security chips provide robust protection for connected assets, benefiting from hardware immutability and compliance with industry standards while being ready to design-in quickly and efficiently aided by a capable supplier.



