Be secure, be safe
Steve Rogerson explores the issues that will be raised in the automotive security session at Embedded World.
One of the blights of the past 30 years as the world has become more connected, has been groups of people determined to exploit that scenario - either for mischievous fun or for more malicious and sinister reasons. Now, with that connectivity stretching to vehicles, this threat has the potential not just for serious disruption but to be life threatening for drivers.
As we move towards a future that will feature autonomous vehicles as a regular sight on our roads, the industry is already wrestling with the massive safety implications which that brings. However, following some prominent car hacks in the past couple of years, security now has to go hand in hand with safety. Already this is being reflected in the next edition of the ISO26262 functional safety standard, which will bring in security as an element of functional safety. And at this year’s embedded world in Nuremburg a session will look at the implications of that and the wider issues of automotive security.
Top image: A Lear prototype that the company hopes will protect future vehicles from being attacked by quantum computers
Experts on hand
To open the session, two security experts - Marcus Janke and Peter Laackmann from Infineon - will explore the history of security in other sectors and how the experience gained can help car manufacturers today.
“Both of us have been looking at security since the 1980s,” said Laackmann. “Yet today, with the likes of smart homes and the IoT, the learning curve is just beginning. They are implementing systems and then learning how they are attacked and what can be done to make them secure.”
In the automotive sector, Janke believes it is getting easier for the attacker because of the increase in the number of interfaces. This point was picked up by Mark Richardson, Lead Field Applications Engineer at LDRA.
“The connected car has so much external communications that the attack surface is very large,” said Richardson. “There will be a lot of people trying to hack into cars and we have to learn from the experience of other domains.”
A major problem is the way the different systems within the car will also be connected. Modern infotainment systems will have access to the internet to download music and films as well as navigation and traffic information. Some of this will be needed by the driver assistance systems and these need to be connected to the controls of the car. The potential for trouble is clear.
“They are putting all this together in a central control system because they all depend on each other,” said Laackmann, “yet they have to be handled differently because they follow different standards.”
And these standards change. Vehicles tend to have longer lifetimes than computers. Many of the new cars today will still be on the road 20 years from now, by which time the attackers will have learned many new ways to exploit vulnerabilities.
“This means the underlying security needs to be standardised in a way that it can be updated,” said Laackmann. “We also have to have a secure updating system.”
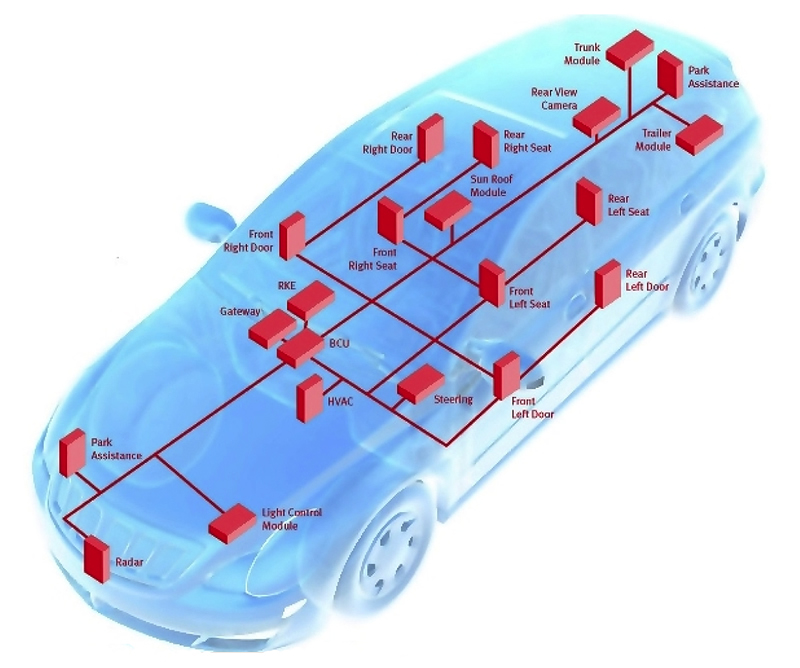
Above: Infineon has identified these as potentially rewarding attack points on a car
Coding standards
Richardson believes the starting point has to be the actual software, making sure it is written to established coding standards to reduce its vulnerability to being hacked. He advocates the use of coding standards such as Misra, which has already amended its guidelines with an additional 14 covering security.
“There is a huge risk here,” he said. “There will always be a weak point and that will let them get in and control cars. For example, the cars will use GPS so what happens if someone flies a drone overhead that emits a really strong signal that disrupts the GPS?”
For that reason he said it was important not only to make sure the software did not do something that it was not intended to do but it had to be reviewed - looking at other vulnerabilities.
“If it gets data from the GPS it has to check to make sure they make sense,” he said. “Basic coding standards will help to make sure the software will not crash and that it makes sure everything is within range.”
Car makers are also adopting open source software such as Genivi and Linux because of the benefits this brings in the amount of development work that already exists when it comes to security as well as other features. However, the wide knowledge of these systems also extends to the potential hackers, a point that will be made by Andrei Kholodnyi, Senior Architect at Intel subsidiary Wind River.
“People know open source systems,” he said. “They know what is inside and that makes it easier for them to use the vulnerabilities that exist. They know how to penetrate these systems.”
In contrast, more proprietary systems often need to be reverse engineered before the vulnerabilities can be discovered.
“However, if you put in the right security policy from step one, then it will be secure whether it is open or closed,” he said.
Future threats
Some threats do not yet exist but could do soon. For example, quantum computers may be able to compromise today’s public key cryptographic algorithms within the lifetime of modern vehicles. It is this issue that Francesc Fons, an Electronics Engineer at Lear, will explore in his talk.
“We have a project in Spain,” he said, “to implement a secure design for an automotive ECU. We aim to explore post-quantum cryptography that can withstand cyber attacks by quantum computing. These, it is believed, will be able to break existing security systems.”
He said that within the 15 to 20 years that today’s cars would be on the road quantum computing would be a fact.
“We need to be prepared in case it is used,” he said. “We are making use of classic cryptography but applying that to quantum computing cryptography, the standards for which have not yet been designed. This means we need to be flexible so we can adapt when they are available.”
The company is using a Xilinx ARM-based multi-core processor on which it is embedding the security, making use of the on-chip programmable logic and communications options.
“We have a system where we can run some tasks in software and some in hardware to offload them from the main processor,” he said. “This is a prototype and not a commercial product but we have developed it to get feedback. We will be presenting our results at the conference.”
Response
The car manufacturers and their suppliers are taking security issues seriously as they want the trust of the public not just for future autonomous vehicles but for all the advanced driver assistance systems that are being introduced today. And to do that they are seeking the help of some of those experienced in causing the problems.
“Some are employing hackers to try to protect the software,” said Richardson. “But at the end of the day it is very difficult to make things secure. I don’t think they can make them totally secure. We have seen what has happened with personal computers - people are still finding new vulnerabilities.”
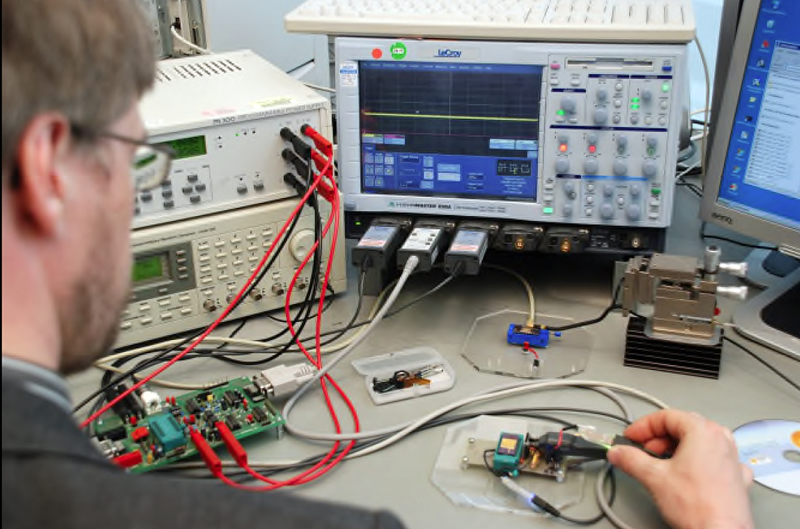
Above: Laboratory attack set-up showing the use of a differential power analysis against a microcontroller
Janke added: “Even things like tyre pressure monitors are potential interfaces. It is hard to figure out how to protect all these interfaces. They will always look for the weakest point.”
And Kholodnyi said: “It is good that the automotive industry has registered these threats. There are various organisations working on these in different areas. There is standardisation going on about how to address cyber security threats.”
Conclusion
As cars become more connected, much more functionality and enjoyment will be brought to drivers and passengers, but with this connectivity lurks a danger, that of the car being hacked. This will not just be an inconvenience but can have serious safety implications as driver assistance systems could be put under external control. Thankfully, the industry is becoming more aware of the threat, and it needs to if it is going to win over the public to the prospect of autonomous vehicles.


